Deploy Book Management Microservices With Istio Service Mesh¶
Now that we understand how services can become part of the Istio service mesh, let's create a book management microservice application using Istio service mesh.
Prerequisite¶
To follow this tutorial, you'll require a domain and, additionally, an SSL certificate for the domain and its subdomains.
-
Register a Route 53 Domain
Go to AWS Console and register a Route 53 domain. You can opt for a cheaper TLD (top level domain) such as
.linkNote
It usually takes about 10 minutes but it might take about an hour for the registered domain to become available.
-
Request a Public Certificate
Visit AWS Certificate Manager in AWS Console and request a public certificate for your domain and all the subdomains. For example, if you registered for a domain
example.comthen request certificate forexample.comand*.example.comNote
Make sure you request the certificate in the region where your EKS cluster is in.
-
Validate the Certificate
Validate the requested certificate by adding
CNAMErecords in Route 53. It is a very simple process. Go to the certificate you created and click onCreate records in Route 53. TheCNAMEswill be automatically added to Route 53.Note
It usually takes about 5 minutes but it might take about an hour for the certificate to be ready for use.
Now that you have everything you need, let's move on to the demonstration.
Docker Images¶
Here are the Docker Images used in this tutorial:
- reyanshkharga/book-management:book-details
- reyanshkharga/book-management:book-genres
- reyanshkharga/book-management:book-web
Note
-
reyanshkharga/book-management:book-genresis a Node.js backend app that uses MongoDB to store and retrieve data, providing a list of books for each genre.Environment Variables:
MONGODB_URI(Required)
-
reyanshkharga/book-management:book-detailsis a Node.js backend app that uses MongoDB to store and retrieve data, providing details for a given book. It also calls thebook-genresmicroservice to return the list of books for a given genre.Environment variables:
MONGODB_URI(Required)REACT_APP_AGENRES_API_ENDPOINTPI_ENDPOINT(Required)
-
reyanshkharga/book-management:book-webis the frontend for book management application.Environment variables:
REACT_APP_API_ENDPOINT(Required)
Objective¶
We are going to deploy the following microservices on our EKS kubernetes cluster:
- Book Details Database microservice
- Book Genres Database microservice
- Book Details microservice
- Book Genres microservice
- Book Web microservice
The following diagram illustrates the communication between microservices:
graph LR
A(Book Web) --> B(Book Details);
B --> C(Book Genres);
B -.-> BD[("Book Details
Database")];
C -.-> CD[("Book Genres
Database")];Note
We will use the same load balancer for all microservices because using more load balancers will be expensive since load balancers are charged hourly. We can achieve this using IngressGroup.
Step 1: Deploy Book Genres Database Microservice¶
Let's create the kubernetes objects for our Book Genres Database microservice as follows:
Notice the istio-injection: enabled label in the namespace object. This will ensure all objects in the namespace are part of the Istio service mesh.
Assuming your folder structure looks like the one below:
|-- manifests
| |-- book-genres-db
│ | |-- 00-namespace.yml
│ | |-- configmap.yml
│ | |-- deployment-and-service.yml
│ | |-- storageclass.yml
│ | |-- pvc.yml
Let's apply the manifests to create the kubernetes objects for Book Genres Database microservice:
This will create the following kubernetes objects:
- A namespace named
book-genres-db - A
StorageClass(SC) for dynamic provisioning of persistent volume - A
PersistentVolumeClaim(PVC) in thebook-genres-dbnamespace - MongoDB deployment in the
book-genres-dbnamespace - MongoDB service in the
book-genres-dbnamespace
We are using Amazon EBS to persist the MongoDB data. EBS is provisioned dynamically using AWS EBS-CSI driver.
With persistent volume even if the MongoDB pod goes down the data will remain intact. When the new pod comes up we'll have the access to the same data.
We are also using configmap to populate data in the MongoDB database.
Verify if the resources were created successfully:
# List all resources in book-genres-db namespace
kubectl get all -n book-genres-db
# List StorageClass
kubectl get sc
# List PersistentVolume
kubectl get pv
# List PersistenvVolumeClaim
kubectl get pvc -n book-genres-db
Verify if MongoDB is working as expected:
# Start a shell session inside the book-genres-db container
kubectl exec -it <mongodb-pod-name> -n book-genres-db -- bash
# Start the mongo Shell to interact with MongoDB
mongo
# List Databases
show dbs
# Switch to a Database
use <db-name>
# List collections
show collections
Step 2: Deploy Book Details Database Microservice¶
Let's create the kubernetes objects for our Book Details Database microservice as follows:
Notice the istio-injection: enabled label in the namespace object. This will ensure all objects in the namespace are part of the Istio service mesh.
Assuming your folder structure looks like the one below:
|-- manifests
| |-- book-details-db
│ | |-- 00-namespace.yml
│ | |-- configmap.yml
│ | |-- deployment-and-service.yml
│ | |-- storageclass.yml
│ | |-- pvc.yml
Let's apply the manifests to create the kubernetes objects for Book Details Database microservice:
This will create the following kubernetes objects:
- A namespace named
book-details-db - A
StorageClass(SC) for dynamic provisioning of persistent volume - A
PersistentVolumeClaim(PVC) in thebook-details-dbnamespace - MongoDB deployment in the
book-details-dbnamespace - MongoDB service in the
book-details-dbnamespace
We are using Amazon EBS to persist the MongoDB data. EBS is provisioned dynamically using AWS EBS-CSI driver.
With persistent volume even if the MongoDB pod goes down the data will remain intact. When the new pod comes up we'll have the access to the same data.
We are also using configmap to populate data in the MongoDB database.
Verify if the resources were created successfully:
# List all resources in book-details-db namespace
kubectl get all -n book-details-db
# List StorageClass
kubectl get sc
# List PersistentVolume
kubectl get pv
# List PersistenvVolumeClaim
kubectl get pvc -n book-details-db
Verify if MongoDB is working as expected:
# Start a shell session inside the book-details-db container
kubectl exec -it <mongodb-pod-name> -n book-details-db -- bash
# Start the mongo Shell to interact with MongoDB
mongo
# List Databases
show dbs
# Switch to a Database
use <db-name>
# List collections
show collections
Step 3: Deploy Book Genres Microservice¶
Let's create the kubernetes objects for our Book Genres microservice as follows:
Notice the istio-injection: enabled label in the namespace object. This will ensure all objects in the namespace are part of the Istio service mesh.
Assuming your folder structure looks like the one below:
|-- manifests
| |-- book-genres
│ | |-- 00-namespace.yml
│ | |-- deployment-and-service.yml
│ | |-- ingress.yml
Let's apply the manifests to create the kubernetes objects for Book Genres microservice:
This will create the following kubernetes objects:
- A namespace named
book-genres - Book Genres deployment in the
book-genresnamespace - Book Genres service in the
book-genresnamespace - Ingress for Book Genres service
The ingress creates an internet-facing load balancer and the SSL certificate is attached to the load balancer.
Note that the certificate is automatically discovered with hostnames from the ingress resource. Also, a Route 53 record is added for the host. This is all done by the AWS Load Balancer Controller and ExternalDNS.
Verify if the resources were created successfully:
# List all resources in book-genres namespace
kubectl get all -n book-genres
# List ingress in book-genres namespace
kubectl get ing -n book-genres
Go to AWS console and verify if the load balancer was created and a record was added to Route 53 for the host specified in ingress.
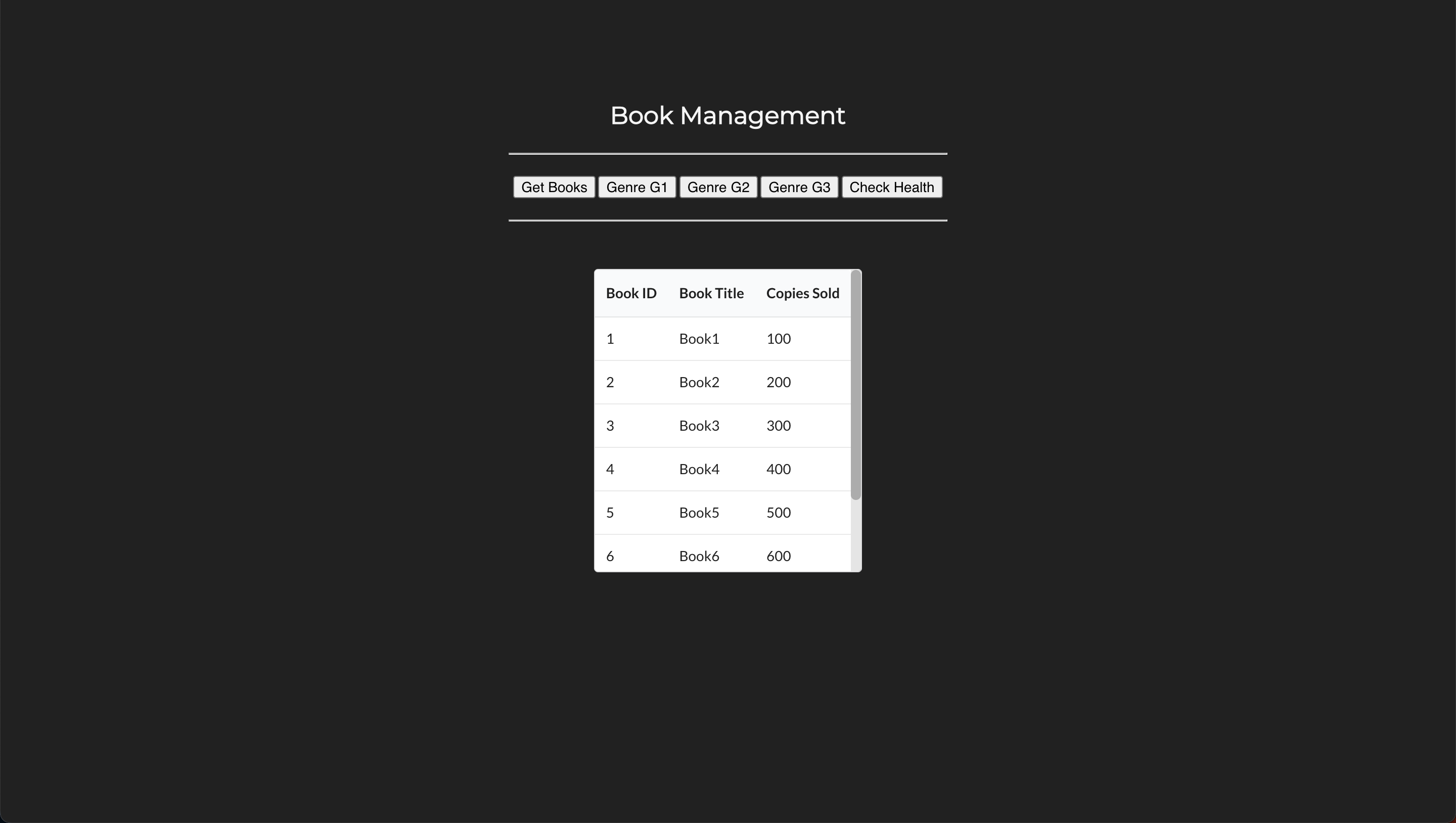
Open any browser on your local host machine and hit the URL to access the book genres service:
Step 4: Deploy Book Details Microservice¶
Let's create the kubernetes objects for our Book Details microservice as follows:
Notice the istio-injection: enabled label in the namespace object. This will ensure all objects in the namespace are part of the Istio service mesh.
Assuming your folder structure looks like the one below:
|-- manifests
| |-- book-details
│ | |-- 00-namespace.yml
│ | |-- deployment-and-service.yml
│ | |-- ingress.yml
Let's apply the manifests to create the kubernetes objects for Book Details microservice:
This will create the following kubernetes objects:
- A namespace named
book-details - Book Details deployment in the
book-detailsnamespace - Book Details service in the
book-detailsnamespace - Ingress for Book Details service
The ingress creates an internet-facing load balancer and the SSL certificate is attached to the load balancer.
Note that the certificate is automatically discovered with hostnames from the ingress resource. Also, a Route 53 record is added for the host. This is all done by the AWS Load Balancer Controller and ExternalDNS.
Verify if the resources were created successfully:
# List all resources in book-details namespace
kubectl get all -n book-details
# List ingress in book-details namespace
kubectl get ing -n book-details
Go to AWS console and verify if the existing load balancer was used and a record was added to Route 53 for the host specified in ingress.
Open any browser on your local host machine and hit the URL to access the book details service:
Step 5: Deploy Book Web Microservice¶
Let's create the kubernetes objects for our Book Web microservice as follows:
Notice the istio-injection: enabled label in the namespace object. This will ensure all objects in the namespace are part of the Istio service mesh.
Assuming your folder structure looks like the one below:
|-- manifests
| |-- book-web
│ | |-- 00-namespace.yml
│ | |-- deployment-and-service.yml
│ | |-- ingress.yml
Let's apply the manifests to create the kubernetes objects for Book Web microservice:
This will create the following kubernetes objects:
- A namespace named
book-web - Book Web deployment in the
book-webnamespace - Book Web service in the
book-webnamespace - Ingress for Book Web service
The ingress creates an internet-facing load balancer and the SSL certificate is attached to the load balancer.
Note that the certificate is automatically discovered with hostnames from the ingress resource. Also, a Route 53 record is added for the host. This is all done by the AWS Load Balancer Controller and ExternalDNS.
Verify if the resources were created successfully:
# List all resources in book-web namespace
kubectl get all -n book-web
# List ingress in book-web namespace
kubectl get ing -n book-web
Go to AWS console and verify if the existing load balancer was used and a record was added to Route 53 for the host specified in ingress.
Open any browser on your local host machine and hit the URL to access the book web service:
Verify if everything is properly and you can interact with book web frontend service and get the book and genre details.